Cybercriminals are upping their game in 2025 with smarter AI and stealthier ransomware targeting Mac users, leaving defenders scrambling to keep up.
The year 2025 may mark the turning point for AI’s role in cybersecurity, according to a recent report from Malwarebytes. While generative AI tools like ChatGPT have made minor waves since their debut, their capabilities have largely been limited to assisting with coding and research tasks.
However, the arrival of agentic AI — artificial intelligence capable of acting autonomously and solving complex tasks — is set to change this dynamic.
A double-edged sword
Agentic AI represents a leap beyond generative tools, giving defenders the ability to automate time-intensive tasks like network monitoring, patching vulnerabilities, and identifying threats. Agents could help close the persistent skills gap in cybersecurity.
For example, AI agents could manage overnight threat detection, handle real-time anomaly tracking, and prioritize patch deployments without constant human oversight.
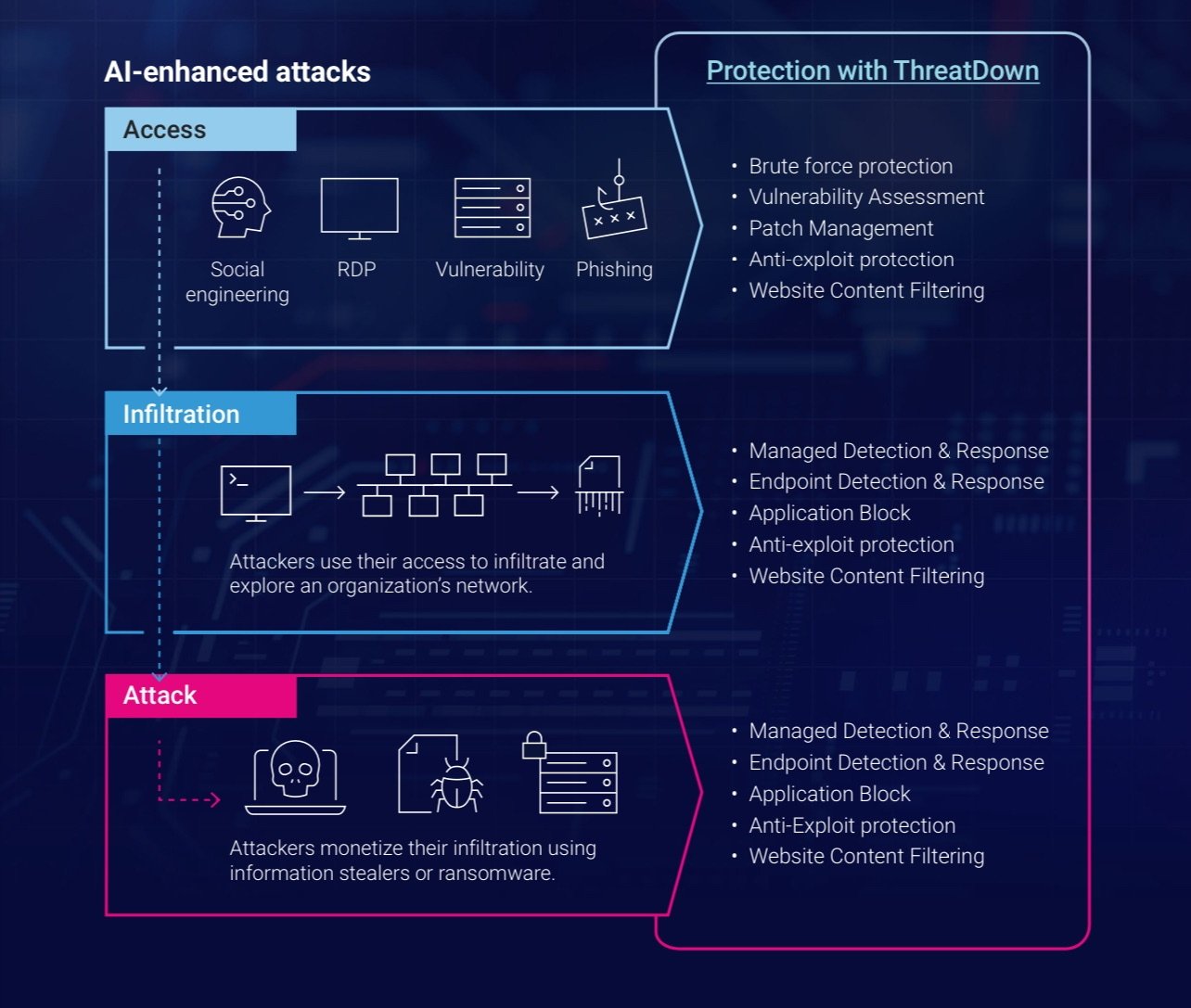
However, the same technology could empower attackers to scale operations. Cybercriminals may use agentic AI to carry out simultaneous ransomware attacks, craft sophisticated phishing campaigns, and even breach networks autonomously.
Ransomware’s evolving tactics
Ransomware continues to dominate as the most lucrative cybercrime, with a 13% rise in attacks in 2024. The largest ransom payment on record — $75 million — occurred in 2024 and was paid to the Dark Angels group from an unknown Fortune 50 company.
However, the ransomware ecosystem is shifting, with major players like LockBit and ALPHV losing influence and smaller, “dark horse” gangs stepping into the spotlight.
These smaller groups have democratized ransomware, making tools and techniques more accessible to cybercriminals. As a result, attacks are not only increasing but also becoming faster and more sophisticated.
Many now rely on stealth, executing entire attack chains, from gaining access to encrypting data, within hours. On macOS, this trend is amplified by the rise of advanced information stealers like Poseidon and Atomic Stealer.
These stealers exploit malvertising campaigns to infiltrate systems and steal sensitive data such as passwords and cryptocurrency wallets.
Macs are increasingly targeted
In recent years, macOS has seen a notable increase in targeted cyberattacks, correlating with its growing adoption in personal and corporate environments. In 2024, the emergence of sophisticated threats like the Banshee macOS Stealer highlighted the platform’s vulnerability to advanced attacks.
When it comes to AI, phishing scams are getting harder to spot, and Mac users aren’t immune. Cybercriminals are using AI to craft emails that mimic messages from Apple, financial institutions, or workplace IT teams.
AI tools can analyze email patterns to generate highly convincing messages, complete with personalized details that make them seem authentic.
Meanwhile, AI-driven malvertising campaigns ensure that fake ads promoting popular Mac software, like productivity apps or security tools, appear at the top of search results. With AI refining these attacks in real-time, traditional red flags like poor grammar or generic messages are no longer reliable warning signs.
How to defend against AI threats
To tackle the rising threats, cybersecurity teams need to rethink their strategies. Using AI-driven tools can help bridge the skills gap by automating threat detection and response.
Enhancing endpoint security is also essential, where advanced solutions can identify suspicious behavior. Securing access points is another priority, starting with disabling remote desktop protocols and limiting tools vulnerable to exploitation.
Finally, staff training remains crucial — teams must be equipped to recognize phishing attempts and social engineering tactics to stay ahead of attackers.